
it-risk-management.com
TIK IT Risk Frameworkit risk management
http://www.it-risk-management.com/

it risk management
http://www.it-risk-management.com/
TODAY'S RATING
>1,000,000
Date Range
HIGHEST TRAFFIC ON
Sunday
LOAD TIME
0.8 seconds
16x16
32x32

64x64

128x128
The Suits
Trevor Kennedy
Westf●●●●● Road
Lo●●on , E14 3AG
GB
View this contact
The Suits
Trevor Kennedy
Westf●●●●● Road
Lo●●on , E14 3AG
GB
View this contact
1&1 Internet Ltd.
Hostmaster ONEANDONE
10-14●●●●● Road
Sl●●gh , BRK, SL1 3SA
GB
View this contact
12
YEARS
0
MONTHS
23
DAYS

1 & 1 INTERNET AG
WHOIS : whois.schlund.info
REFERRED : http://1and1.com
PAGES IN
THIS WEBSITE
9
SSL
EXTERNAL LINKS
7
SITE IP
141.0.159.102
LOAD TIME
0.798 sec
SCORE
6.2
TIK IT Risk Framework | it-risk-management.com Reviews
https://it-risk-management.com
it risk management
 it-risk-management.com
it-risk-management.com
IT Risk Management - Threats
http://www.it-risk-management.com/threats.html
Online Cyber Security Magazine. GPG 13 - Protective Monitoring. If you would like to stay in touch sign up for our Newletter below! What Threats are there to the Organisations Assets? The next component to consider is what Threat you have to your Asset. Threat is measured as a percentage, ranging from zero percent, implying no threat, to one hundred percent, implying a constant threat. When considering Enterprise IT Risk management we need to understand if our organisation has a threat to the organisatio...
IT Risk Management - Vulnerabilities
http://www.it-risk-management.com/Vulnerabilities.html
Online Cyber Security Magazine. GPG 13 - Protective Monitoring. If you would like to stay in touch sign up for our Newletter below! Vulnerabilities are weaknesses within your control system. No control system is 100% perfect, 100% the time, you can have all the IT Security Countermeasures in the world, but if your Users handover their password and username to any person on the other end of a telephone line claiming to be from the IT Helpdesk, you have a weakness/vulnerability within your system. This is ...
IT Risk Calculations
http://www.it-risk-management.com/it-risk-calculations.html
Online Cyber Security Magazine. GPG 13 - Protective Monitoring. If you would like to stay in touch sign up for our Newletter below! Lets take a look at some Sample IT Risk Calculations. If we evaluate those organisations that have been breached and calculate the maturity of their control systems we can determine an industry average. Fortunately a significant amount of this work has been completed for us by Verizon, with their Annual Verizon Breach Report. Difficulty to Compromise IT Controls. Moderate: s...
About IT Risk Management
http://www.it-risk-management.com/about.html
Online Cyber Security Magazine. GPG 13 - Protective Monitoring. If you would like to stay in touch sign up for our Newletter below! This website is run and owned by CYSEC. CYSEC is a IT Security and Risk Content Publisher, that also provides Cyber Security Consulting, Development and Implementation Company. We specialise in security policy creation, security control implementation and penetration testing, on top of our unique security content business. Adam is our Sales Manager and is the first point of ...
Security Information Management
http://www.it-risk-management.com/it-risk-measurement.html
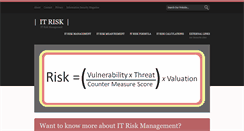
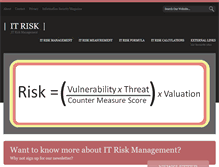
Online Cyber Security Magazine. GPG 13 - Protective Monitoring. If you would like to stay in touch sign up for our Newletter below! How Do You Measure IT Risk? There are over eighty different risk frameworks for measuring enterprise risk, one of the more popular is COSO, which comes from The Committee of Sponsoring Organizations (COSO) of The Treadway Committee. IT Risk Framework - TIK. The potential Threats {t}. To the organisation, the Countermeasures {cms}. In the IT Control System implementation.
TOTAL PAGES IN THIS WEBSITE
9
![]() enterprise-risk-management.org
enterprise-risk-management.org
Types of Risks
http://www.enterprise-risk-management.org/risk.php
Online Cyber Security Magazine. GPG 13 - Protective Monitoring. If you would like to stay in touch sign up for our Newletter below! What are the Different Types of Risk? There exist over eighty Enterprise Risk frameworks and a significant number of definitions of Risk, one of the more popular frameworks is the Casualty Actuarial Society model which conceptualised Enterprise Risk Management as continuing across the two dimensions of Risk Type and Risk Management Processes. Once Risks have been identified ...
![]() enterprise-risk-management.org
enterprise-risk-management.org
About Us
http://www.enterprise-risk-management.org/about.php
Online Cyber Security Magazine. GPG 13 - Protective Monitoring. If you would like to stay in touch sign up for our Newletter below! This website is run and owned by CYSEC. CYSEC is a IT Security and Risk Content Publisher, that also provides Cyber Security Consulting, Development and Implementation Company. We specialise in security policy creation, security control implementation and penetration testing, on top of our unique security content business. Adam is our Sales Manager and is the first point of ...
![]() enterprise-risk-management.org
enterprise-risk-management.org
Internal Audit
http://www.enterprise-risk-management.org/Internal_audit.php
Online Cyber Security Magazine. GPG 13 - Protective Monitoring. If you would like to stay in touch sign up for our Newletter below! What is the Role of Internal Audit? It is unlikely the Internal Auditors will be involved in the Risk Functions, outside of the audit process, as it would be a conflict of interest for them to define risk measurements. However an organisation with a strong audit function should encourage the internal audit team to challenge defined measurements of success. This review would ...
![]() enterprise-risk-management.org
enterprise-risk-management.org
Risk Functions
http://www.enterprise-risk-management.org/Risk_Functions.php
Online Cyber Security Magazine. GPG 13 - Protective Monitoring. If you would like to stay in touch sign up for our Newletter below! What Risk Functions Should Your Organisation Have? Most organisations will have a number of Risk functions, such as IT Risk Management, Currency Risk managers, closely related to the Financial Risk Managers to identify and manage explicit Risk. The following Risk Functions would be common in large enterprises:. Typically would include Chief Financial Officer and senior accou...
![]() enterprise-risk-management.org
enterprise-risk-management.org
Enterprise Risk management
http://www.enterprise-risk-management.org/enterprise_risk_management.php
Online Cyber Security Magazine. GPG 13 - Protective Monitoring. Enterprise Risk Management Overview. If you would like to stay in touch sign up for our Newletter below! What is Enterprise Risk Management? ERM provides a framework for Risk Management, which usually involves identifying explicit events or circumstances relevant to the organisation's objectives (risks verse opportunities), assessing the probability and magnitude of impact, determining a response strategy, and monitoring progress. There are ...
![]() enterprise-risk-management.org
enterprise-risk-management.org
TIK IT Risk Framework
http://www.enterprise-risk-management.org/index.php
Online Cyber Security Magazine. GPG 13 - Protective Monitoring. Want to know more about ERM? Why not sign up for our newsletter? Enterprise Risk Management, often referred to as ERM is a set of processes and methods utilised by organisations to manage risks and exploit opportunities associated with the achievement of their objectives. View The Full Article on ERM ». View The Full Article on Risk Types ». View The Full Article on Risk Functions ». View The Full Article on Internal Audit ». This website is...
TOTAL LINKS TO THIS WEBSITE
7
IT Risikoconsult
das IT-Risiko-Portal - Das IT-Risikoportal
Herzlich Willkommen auf IT-Risikomanagement.com. Dies soll ein zentraler Informationspunkt zum "jungen" Thema IT-Risikomanagement werden. "Jung" - da Risiken zum täglichen Leben gehören und folgerichtig in diesem Themengebiet seit der ersten elektronischen Datenverarbeitung mehr oder weniger berücksichtigt wurden. Neu an dem Thema sind somit nicht dessen Inhalte, sondern vielmehr die ganzheitliche Betrachtungsweise, die zu einem quantifizierbaren Ergebnis führen soll. Letzte Änderung am 30.04.2017.
Domain Default page
If you are seeing this message, the website for is not available at this time. If you are the owner of this website, one of the following things may be occurring:. You have not put any content on your website. Your provider has suspended this page. Please login to to receive instructions on setting up your website. This website was created using our Parallels Panel product. We offer a full line of Billing, Sitebuilder and cloud computing tools. Please visit www.parallels.com. To find out more information.
web8 @ rz1-mcm-web001.mcm.local
Hier entstehet eine neue Internet-Seiten des Benutzers web8. Auf rz1-mcm-web001.mcm.local.
TIK IT Risk Framework
Online Cyber Security Magazine. GPG 13 - Protective Monitoring. Want to know more about IT Risk Management? Why not sign up for our newsletter? One of the most crucial aspects of an Enterprise Risk Management strategy is IT Risk Management. In a more connected world, Information Security is becoming a critical success factor for organisations. View The Full Article on IT Risk Management ». View The Full Article on IT Risk Measurement». View The Full Article on Valuation at Risk ». Vulnerabilities are wea...
IT Risk KM Consulting
IT Risk KM Consulting GmbH, Ihr Partner für angemessene und nachhaltige Lösungen beim Management von:. Beratung bei Aufbau und Betrieb eines Informationssicherheits -. Ausbildung und Übungen in IT-. Unterstützung bei der Ausarbeitung von Sicherheits-. Policies und Sicherheitskonzepten sowie zur Überbrückung bei vakanten Sicherheitspositionen. Steuerung und Durchführung des Risk Managements der Informationstechnologie und der Informationssicherheit. Mit langjähriger Erfahrung in der Informations-.
RiskNET - The Risk Management Network
Cash Flow at Risk. Jakob I. Bernoulli. Andrew W. Lo. Hyman P. Minsky. Robert J. Shiller. Prof Dr. Bruno Brühwiler. Prof Dr. Roland Franz Erben. Prof Dr. Robert Finke. Prof Dr. Werner Gleißner. Prof Dr. Michael Huth. Prof Dr. Matthias Müller-Reichart. Prof Dr. Josef Scherer. Vom weißen Elefanten in digitalen Zeiten. Oh Wunder: Datenlecks und Intransparenz. Frank Romeike Andreas Eicher [RiskNET]. Cyber-Kriminalität: Das unterschätzte Risiko. Deutscher Corporate Governance Kodex. Die Krise geht weiter.
RiskNET - The Risk Management Network
Cash Flow at Risk. Jakob I. Bernoulli. Andrew W. Lo. Hyman P. Minsky. Robert J. Shiller. Prof Dr. Bruno Brühwiler. Prof Dr. Roland Franz Erben. Prof Dr. Robert Finke. Prof Dr. Werner Gleißner. Prof Dr. Michael Huth. Prof Dr. Matthias Müller-Reichart. Prof Dr. Josef Scherer. Vom weißen Elefanten in digitalen Zeiten. Oh Wunder: Datenlecks und Intransparenz. Frank Romeike Andreas Eicher [RiskNET]. Cyber-Kriminalität: Das unterschätzte Risiko. Deutscher Corporate Governance Kodex. Die Krise geht weiter.
Information Technology Risk Advisory Services
Information Technology Risk Advisory Services. A website created by GoDaddy’s Website Builder.
The Sponsored Listings displayed above are served automatically by a third party. Neither Parkingcrew nor the domain owner maintain any relationship with the advertisers. In case of trademark issues please contact the domain owner directly (contact information can be found in whois).
SOCIAL ENGAGEMENT